Shift-Left Security in Kubernetes
Security can’t be an afterthought in Kubernetes. In fast-moving DevOps pipelines, leaving security checks until production means vulnerabilities are caught too late. The solution is Shift-Left Security — bringing security earlier into the CI/CD lifecycle.
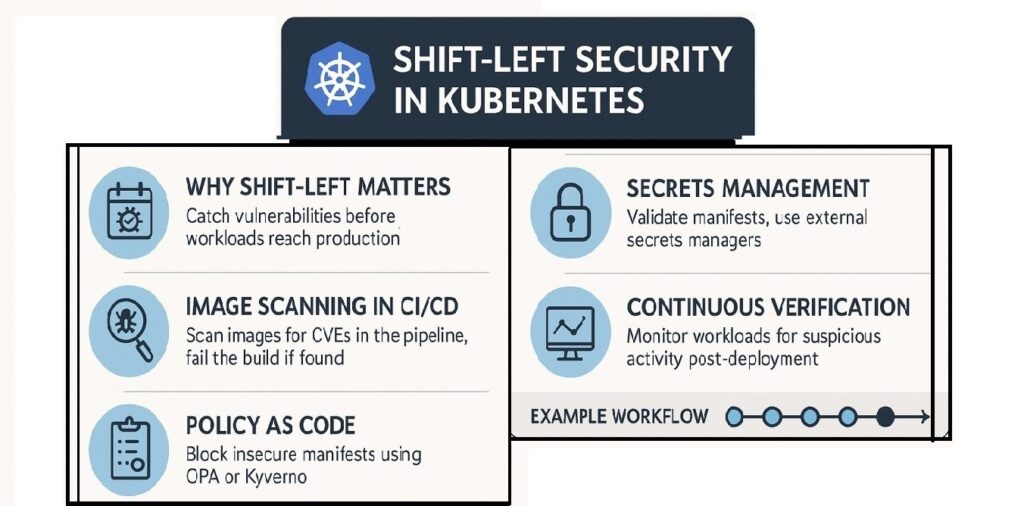
1. Why Shift-Left Matters in Kubernetes
- Containers move from dev to prod in minutes.
- Without security baked into build and deploy, misconfigured RBAC, exposed secrets, and vulnerable images slip into clusters.
- By shifting left, vulnerabilities are caught before workloads hit production.
2. Image Scanning in CI/CD
Use tools like Trivy, Anchore, or Clair to scan container images before they’re deployed.
Example: GitHub Actions step with Trivy.
– name: Scan container image
uses: aquasecurity/trivy-action@master
with:
image-ref: myapp:latest
format: ‘table’
exit-code: ‘1’
ignore-unfixed: true
If critical CVEs are found, the pipeline fails.
3. Policy as Code
Shift-left means enforcing compliance early in the pipeline. Open Policy Agent (OPA Gatekeeper) or Kyverno can block bad manifests before they reach the cluster.
Example: Block privileged containers.
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sPSPNoPrivilegedContainer
metadata:
name: disallow-privileged
spec:
enforcementAction: deny
This prevents engineers from accidentally deploying insecure pods.
4. Secrets Management
Hardcoding secrets in ConfigMaps or environment variables is risky. Shift-left requires:
- Using external secrets managers (HashiCorp Vault, AWS Secrets Manager, External Secrets Operator).
- Validating that manifests don’t include plaintext secrets during CI checks.
5. Continuous Verification
Shift-left doesn’t stop at deployment. Even after workloads are live:
- Prometheus metrics can detect suspicious patterns (e.g., privilege escalation errors).
- Logs and traces help identify anomalous activity.
- KubeHA correlates these signals in real time and suggests remediation.
6. Example Workflow
- Developer pushes new code.
- CI/CD scans image with Trivy.
- Manifest validated by OPA policies.
- Deployment blocked if insecure.
- Once live, KubeHA + Prometheus continuously verify workloads.
Bottom Line: Shift-left security in Kubernetes is about prevention, not reaction. By scanning images, enforcing policies, managing secrets properly, and continuously verifying workloads, DevOps and SRE teams ensure vulnerabilities are caught before they ever reach production.
Follow KubeHA(https://lnkd.in/gV4Q2d4m)for ready-to-use CI/CD templates, policy examples, and automated RCA workflows that bring security earlier into your Kubernetes lifecycle.
Experience KubeHA today: www.KubeHA.com
KubeHA’s introduction, 